Encryption
In cryptography, encryption is the process of obscuring information to make it unreadable without special knowledge
While encryption has been used to protect communications for centuries, only organisations and individuals with an extraordinary need for secrecy have made use of it. In the mid-1970s, strong encryption emerged from the sole preserve of secretive government agencies into the public domain, and is now employed in protecting widely-used systems, such as Internet e-commerce, mobile telephone networks and bank automatic teller machines.
Encryption can be used to ensure secrecy, but other techniques are still needed to make communications secure, particularly to verify the integrity and authenticity of a message; for example, a message authentication code (MAC) or digital signatures. Another consideration is protection against traffic analysis.
Ciphers
A cipher is an algorithm for performing encryption (and the reverse, decryption) - a series of well-defined steps that can be followed as a procedure. An alternative term is encipherment. The original information is known as plaintext, and the encrypted form as ciphertext. The ciphertext message contains all the information of the plaintext message, but is not in a format readable by a human or computer without the proper mechanism to decrypt it; it should resemble random gibberish to those not intended to read it.
Ciphers are usually parameterized by a piece of auxiliary information, called a key. The encrypting procedure is varied depending on the key which changes the detailed operation of the algorithm. Without the appropriate key, the cipher cannot be used to encrypt or decrypt.
"Cipher" is alternatively spelt "cypher"; similarly "ciphertext" and "cyphertext", and so forth. Both spellings have long histories in English.
Ciphers versus codes
In non-technical usage, a "(secret) code" is the same thing as a cipher. Within technical discussions, however, they are distinguished into two concepts. Codes work at the level of meaning - that is, words or phrases are converted into something else. Ciphers, on the other hand, work at a lower level: the level of individual letters, small groups of letters, or, in modern schemes, individual bits. Some systems used both codes and ciphers in one system, using superencipherment to increase the security.
Historically, cryptography was split into a dichotomy of codes and ciphers, and coding had its own terminology, analogous to that for ciphers: "encoding, codetext, decoding" and so on. However, codes have a variety of drawbacks, including susceptibility to cryptanalysis and the difficulty of managing a cumbersome codebook. Because of this, codes have fallen into disuse in modern cryptography, and ciphers are the dominant technique.
Types of cipher
There are a variety of different types of encryption. Algorithms used earlier in the history of cryptography are substantially different from modern methods, and modern ciphers can be classified according to how they operate and whether they use one or two keys.
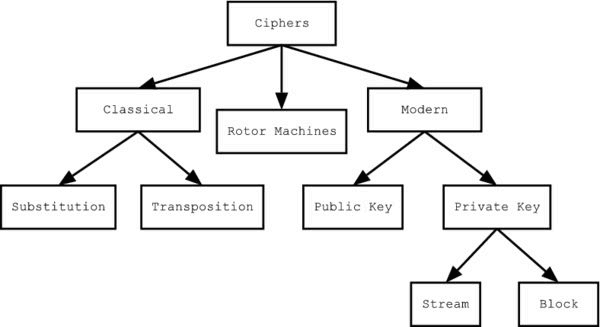
Historical pen and paper ciphers used in the past are sometimes known as classical ciphers. They include substitution ciphers and transposition ciphers. During the early 20th century, more sophisticated machines for encryption were used, rotor machines, which were more complex than previous schemes.
Encryption methods can be divided into symmetric key algorithms and asymmetric key algorithms. In a symmetric key algorithm (e.g., DES and AES), the sender and receiver must have a shared key set up in advance and kept secret from all other parties; the sender uses this key for encryption, and the receiver uses the same key for decryption. In an asymmetric key algorithm (e.g., RSA), there are two separate keys: a public key is published and enables any sender to perform encryption, while a private key is kept secret by the receiver and enables him to perform decryption.
Symmetric key ciphers can be distinguished into two types, depending on whether they work on blocks of symbols usually of a fixed size (block ciphers), or on a continuous stream of symbols (stream ciphers).
This article is licensed under the GNU Free Documentation License.
It uses material from the Wikipedia article "Encryption".
|